Course description
This course will explore types of security threats, both digital and physical, It will cover identity theft, data classification: sharing, privileges, and risk management.
Prerequisites
There are no prerequisites.
Learning Paths
This course is part of the following LearnNowOnline SuccessPaths™:
Security Awareness
Meet the expert
As a certified Microsoft Instructor, Ken has focused his career on various security aspects of computer and network technology since the early 1980s. He has offered a wide variety of IT training and high level consulting projects for Fortune 500 companies globally. Through the course of his extensive career, he has taught a full line of Microsoft, CompTIA, Cisco, and other high level IT Security curricula.
Course outline
Data Classification
Identify Theft (27:51)
- Introduction (00:10)
- What Is Identity Theft? (01:42)
- Other Possibilities (00:59)
- How Does It Happen? (02:56)
- More Identity Theft Methods (05:54)
- How to Defend Yourself (Cont.) (06:34)
- Online Credit Card Use (00:38)
- What Criminals Do with Your Information (01:51)
- Other Things Criminals Do (01:17)
- What Criminals Do with Your Information (Cont.) (01:09)
- How to Know if You're a Victim (00:39)
- Actions to Take if You Are a Victim (01:24)
- Fraud Alerts (01:46)
- Contact Information (00:38)
- Summary (00:08)
Data Classification Part 1 (22:22)
- Introduction (00:08)
- Policies for Data Sharing (04:32)
- Privilege Creep (05:29)
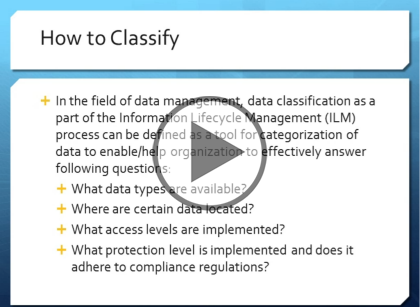
- How to Classify (01:35)
- Information Value (03:31)
- How to Classify (Cont.) (01:36)
- Evaluate and Divide (01:15)
- How to Classify (Cont. Again) (02:45)
- Structured and Unstructured Data (01:19)
- Summary (00:08)
Data Classification Part 2 (17:24)
- Introduction (00:08)
- Data Classification (04:11)
- What Could Happen? (01:54)
- What Type of Policies? (04:44)
- Destroying Data (02:56)
- How to Destroy Data (03:21)
- Summary (00:08)